Configure a user in AWS IAM that is required to use MFA to connect to a bucket in S3 with a policy requiring MFA
You want an IAM user with permissions to access S3 to require input from a MFA device when opening a specific bucket. Create a configuration for AWS CLI that is supported in Cyberduck and Mountain Duck using the S3 (Credentials from AWS Command Line Interface) connection profile or use the AWS S3 (MFA Session Token) connection profile with no additional configuration.
Create a bookmark in Cyberduck or Mountain Duck
Open Preferences… → Profiles in Cyberduck or Mountain Duck.
Enable the AWS S3 (MFA Session Token) connection profile.
Add a new Bookmark in Cyberduck or Mountain Duck and choose AWS S3 (MFA Session Token) connection profile in the protocol dropdown.
Create IAM user with access keys and MFA enabled
In AWS IAM console create a new user.
In Security Credentials, choose Assign MFA device
In Security Credentials, choose Create access key
Ensure the attached policy for the user has S3 access IAM
GetSessionToken permissions.
Add bucket policy to deny access to bucket with no MFA
In AWS S3 console for a new or existing bucket, choose Permissions and then Bucket Policy.
Edit the bucket policy to require MFA for access.
{ "Version": "2012-10-17", "Id": "RequireMFAForS3Access", "Statement": [ { "Sid": "DenyAllAccessWithoutMFA", "Effect": "Deny", "Principal": "*", "Action": "s3:*", "Resource": [ "arn:aws:s3:::<BUCKET_NAME>", "arn:aws:s3:::<BUCKET_NAME>/*" ], "Condition": { "BoolIfExists": { "aws:MultiFactorAuthPresent": "false" } } } ] }
Connect to S3 using the bookmark
Using the AWS Security Token Service (STS) GetSessionToken API, temporary credentials are generated for the user from
static access keys and a MFA device.
When not already configured in the bookmark, enter the static Access Key ID and Secret Access Key configured for the user.
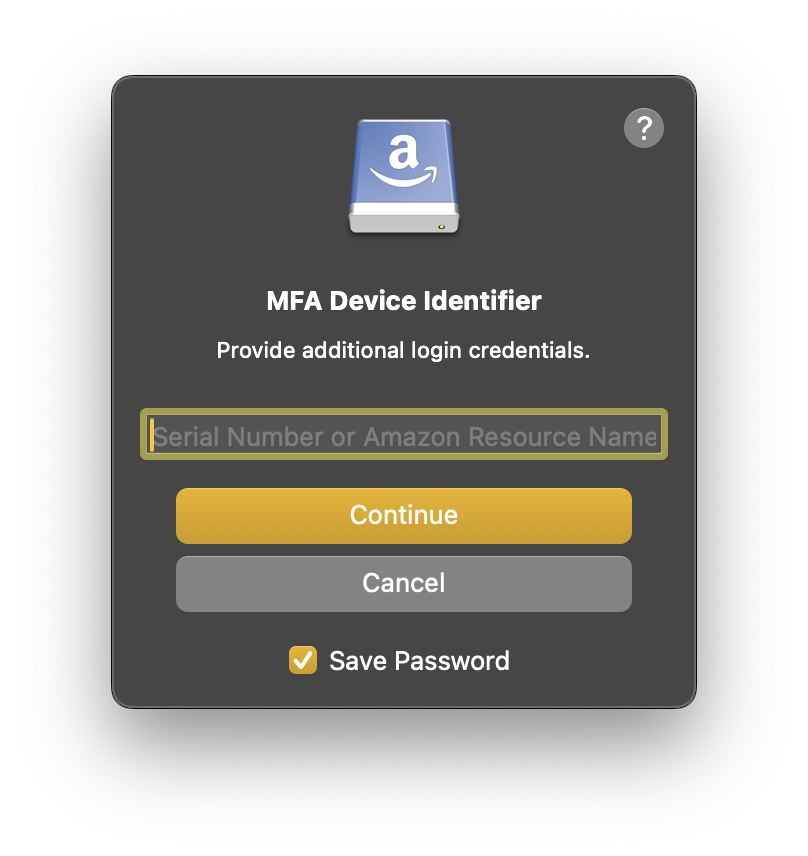
Enter the MFA device identification when prompted.
Tip
Enter the identification number of the MFA device that is associated with the user. The value is either the serial number for a hardware device (such as
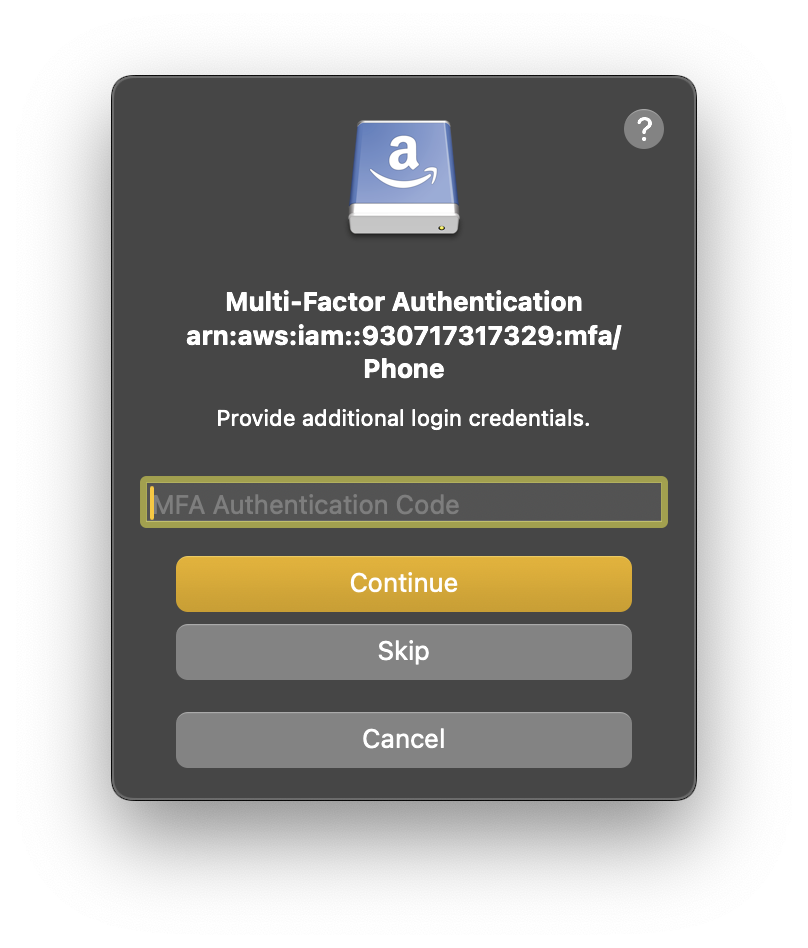
<code>GAHT12345678</code>) or an Amazon Resource Name (ARN) for a virtual device (such as<code>arn:aws:iam::123456789012:mfa/device</code>)Enter the one-time MFA code from your device when prompted.
Troubleshooting
User: arn:aws:iam::123456789012:user/<username> is not authorized to perform: s3:ListBucket on resource: "arn:aws:s3:::<bucket>" with an explicit deny in a resource-based policy.
Attempted to connect to the bucket with access keys not obtained using GetSessionToken and MFA code.
The security token included in the request is invalid.
The access keys used to obtain temporary credentials from AWS Security Token Service (STS) are not valid.